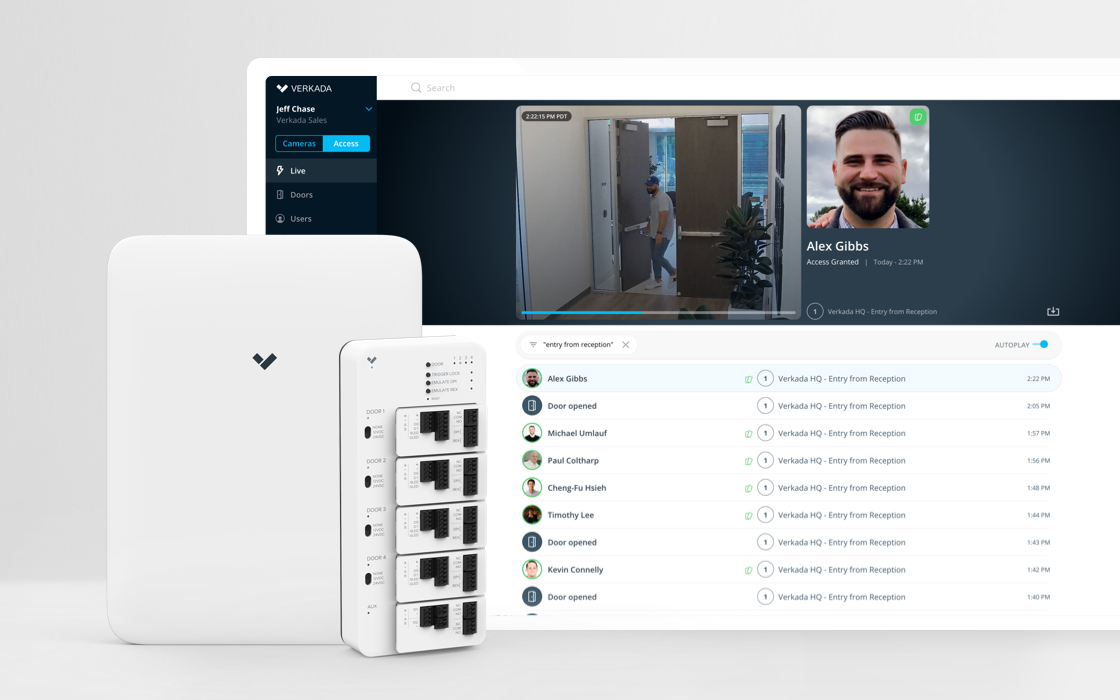
Access Control is a vital part of information security and is defined as the process by which you grant or deny access to your data, property, and other objects. Three elements make up access control: identification, authentication, and authorization.
If you're running a business, managing a team, or protecting sensitive information, you already know this: keeping the wrong people out—and letting the right people in—is everything. That’s what a solid Access Control System is designed to do.
The world of information security is vast. There are endless threats—some visible, some subtle—and a wide array of defenses to counter them. One of the most effective ways to defend your space (digital or physical) is through an Access Control System that spells out clearly who can do what, when, and where.
These systems rely on identifiers (like usernames or ID badges), authentication methods (passwords, biometrics), and a rules engine that determines if someone should get access or not. The goal is simple: keep your critical data, systems, and spaces locked down from unauthorized use—without making life miserable for authorized users.
Let’s walk through how that happens.
Elements of Access Control
Identification:
Think of this as the front door check. Before someone can be let in, you need to know who they are.
Identification is the first step. In a system, it means tagging a user with a unique identity—like a username or ID badge. Once tagged, the system can track what they do, when they log in, where they swipe in, and which systems they touch.
User IDs are the digital version—each one tied to a specific person, role, or profile. They’re like fingerprints in your IT system.
Badges are for physical spaces. These are swipe cards or wearables that grant building or room access. Some badges now double as digital credentials, allowing you to control both physical entry and system access from one place.
Engaging insight:
A visitor walking into a building might show a badge. A remote employee logging into a VPN uses a unique user ID. In both cases, the system’s job is to ask—who are you?
Authentication:
So someone claims to be Jane Doe. Great. But how do you know it’s really her?
Authentication is that second layer. It’s proof. It’s the digital equivalent of “show me your ID and your password, and maybe your face too.”
Traditionally, authentication relied on something you know (like a password). But that’s no longer enough. With cyberattacks evolving, companies now layer in:
- Something you have (like a one-time code sent to your phone)
- Something you are (like a fingerprint or face)
That’s where Biometric Access Control enters the picture—fingerprints, iris scans, facial recognition. It’s fast, hands-free, and hard to fake.
Bonus insight:
Biometrics are widely used at high-security facilities, border controls, and even office buildings. But keep in mind—they’re not foolproof. Factors like lighting, age, or injury can sometimes cause errors. That’s why fallback methods (PINs or backup codes) are essential.
Authorization:
You’ve identified the user. You’ve authenticated them. Now it’s time for the final decision: what are they allowed to do?
This is authorization—defining access rights.
It’s not one-size-fits-all. An intern shouldn’t be able to download financial reports. A contractor doesn’t need access to HR files. That’s why Access Control Security Systems use two main models:
- Access Control Lists (ACLs): Specific permissions assigned to individuals or groups. Great for control, but harder to manage at scale.
- Role-Based Access Control (RBAC): Users get access based on their job title or department. This makes onboarding and transitions smoother.
Real-world example:
In a hospital, a nurse can access patient charts but not billing records. An admin might see financials but not lab results. That’s authorization in action.
Challenges of Access Control
Implementing an Access Control Solution isn’t just plug-and-play. There are real-world headaches and trade-offs. Here’s where things get tricky.
1. Balancing Security and Usability
Too much security slows people down. Too little, and you’re inviting trouble. Finding that sweet spot takes planning.
Make passwords too complex, and people write them on sticky notes. Force frequent logins, and users get annoyed. Biometric login sounds great—until the scanner fails mid-shift.
The fix? Use smart defaults. Require multi-factor authentication only where it matters most. Give users a password vault. Use Physical Access Control for sensitive zones, not the entire building.
2. Managing Access Over Time
Employees switch roles. Projects end. Contractors come and go. But their access often lingers. That’s risky.
Without regular reviews, former staff may still have working credentials. That’s why Access Control Security demands routine audits and automated deprovisioning.
Pro tip:
Use centralized systems that can link access permissions to HR platforms—so when someone leaves, their access shuts down immediately.
3. Keeping Up With Threats
Hackers don’t sleep. And they love weak access points.
Phishing emails, stolen credentials, reused passwords—they're all common entry methods. And once inside, attackers move laterally across systems if controls aren’t strong.
That’s where Zero Trust comes in. Instead of trusting anyone inside the perimeter, the system continuously verifies identity, context, and risk before granting or maintaining access.
Machine learning tools can also help spot unusual access behavior—like a user logging in from two countries within minutes.
More Things to Consider
Let’s throw in a few more useful pointers as you think about your access control strategy:
- Guest access should always be time-limited, easily revoked, and tracked. Don't let third-party vendors access your network unchecked.
- Remote work adds complexity. If your team logs in from home, make sure VPNs, location policies, and device security are in place.
- Physical Access Control needs to tie into emergency protocols. For example, doors should unlock automatically during a fire drill or security threat.
- Unified dashboards help monitor both digital and physical access events in real time. The fewer silos, the faster your response to breaches.
Final Thoughts
Access Control isn’t just about IT. It’s about trust, accountability, and risk management. It affects everyone—from the receptionist swiping into the office to the CTO logging into the server farm. When done right, it quietly keeps your business safe and running smoothly.
But it’s not a one-and-done job. Your Access Control System has to evolve as your organization grows, technology changes, and threats increase.
Need help figuring out what access control looks like for your business? Call us at +1 949-333-1000.
At BCS Consultants, we design secure, scalable Access Control Security Systems that give you peace of mind—and full control.
Frequently Asked Questions (FAQ)
1.What’s the difference between an Access Control System and traditional security methods like locks and keys?
A traditional lock-and-key setup grants physical access—but there’s no visibility, no audit trail, and no way to restrict or revoke access without physically retrieving keys. In contrast, an Access Control System is intelligent and trackable. It can control access to both physical spaces and digital assets, define permissions by role or schedule, and instantly revoke access when needed. It also supports Access Control Authentication tools like PINs, smart cards, or biometrics for higher security.
2.Is Biometric Access Control safe to use?
Yes, when implemented correctly. Biometric Access Control is secure because it uses unique physical traits like fingerprints or facial recognition, which are difficult to replicate. However, it's crucial to store biometric data securely (encrypted and on-device when possible) and have backup authentication options. Biometric systems should also comply with data protection regulations such as GDPR or HIPAA where applicable.
3.Can Access Control Systems be integrated with other security technologies?
Absolutely. Modern Access Control Security Systems are designed to integrate with surveillance cameras, alarm systems, fire detection, visitor management, and even cloud-based platforms. Unified integration gives security teams a real-time, centralized view of access events—making it easier to spot threats and respond quickly. Some advanced Access Control Solutions also support AI-driven analytics for proactive risk detection.
4.How often should we audit our access control policies?
At minimum, access permissions should be reviewed quarterly, especially for sensitive roles or high-security areas. Some organizations adopt automated provisioning and deprovisioning based on HR workflows to reduce risk. Regular audits help prevent access creep, where users gradually accumulate permissions they no longer need—a common gap in access control security.