Security is no longer just about locks and keys; it’s about staying ahead of threats in a world where technology evolves daily. With businesses facing increasing physical and digital risks, implementing a cloud based security system has become essential for safeguarding operations, assets, and sensitive data.
Top 5 Access Control Systems Providers or Companies

Every business and institution understands the need for security—both physical and digital. The modern solution? Access control systems that effectively monitor and manage who can enter specific areas and at what times. These systems help protect valuable assets, confidential data, and secure environments.
How Much Should You Spend on Your Small Business Security System?

As a small business owner, safeguarding your company, employees, and assets is a top priority. While investing in a security system is essential, determining how much to allocate towards it depends on various factors. Considering your security needs and selecting the right security and surveillance solutions can help ensure that your business is protected without overspending.
Enhancing Security: The Applications and Benefits of Facial Recognition Access Control Systems

Face recognition access control transforms security measures across various sectors, providing an innovative solution that leverages advanced biometric technology. These systems offer unparalleled security, convenience, and efficiency, making them an increasingly popular choice for businesses and institutions in California and beyond.
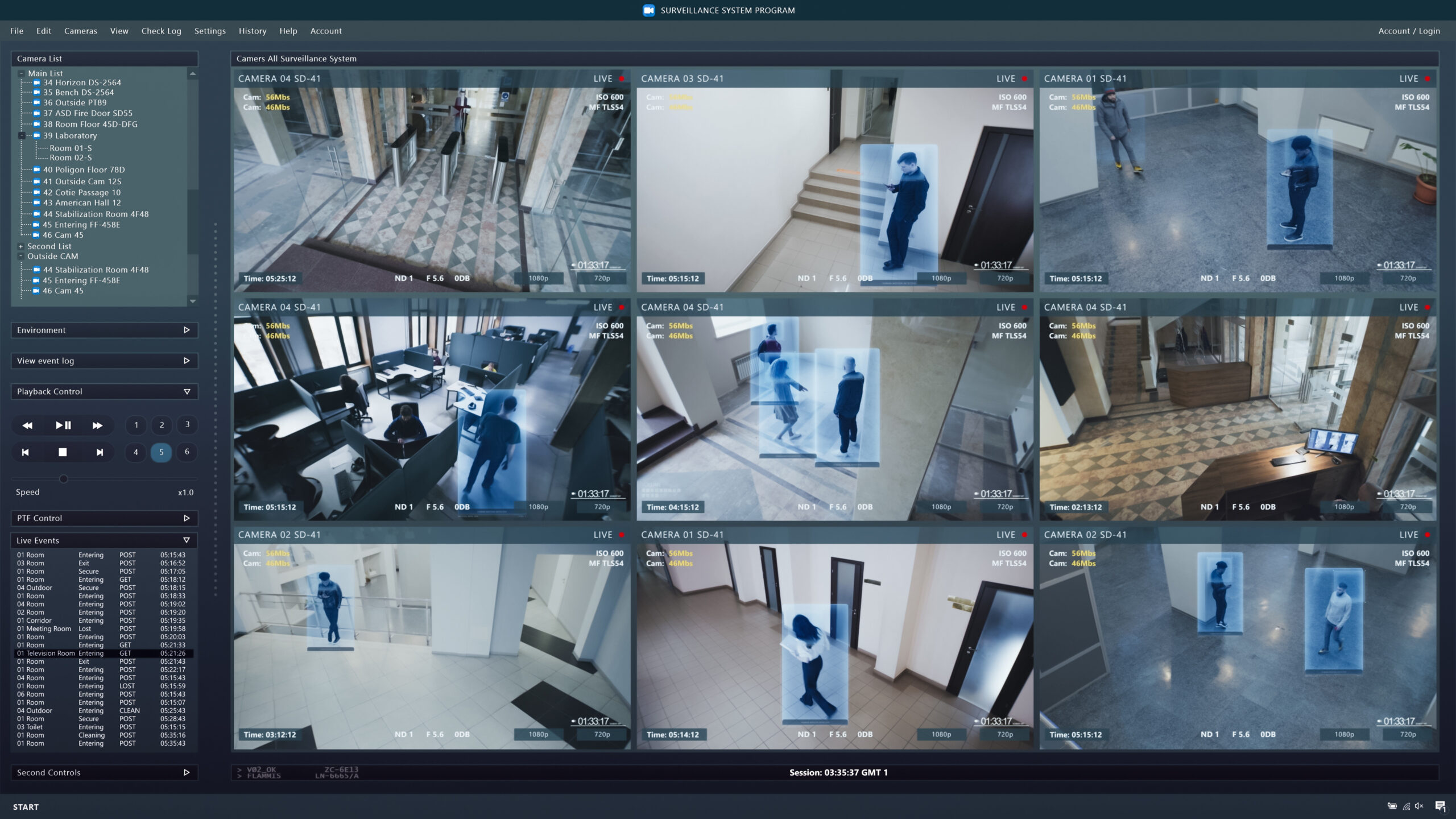
Choosing The Right Small Business Security Camera And Surveillance Systems
How To Choose The Best Door Access Control System For Your Business

In today's increasingly digital and interconnected world, ensuring the security of business premises is more crucial than ever. A door access control system serves as the first line of defense, controlling who can and cannot enter your business. This makes choosing the right system not just a matter of security, but a crucial step in safeguarding your assets, data, and personnel.
How To Choose the Best Commercial Security System for Your Business or Office
In California, guaranteeing the security of your commercial premises is vital due to the high density of business activities and the various threats that come with it. A well-chosen commercial security system not only protects your physical and intellectual property but also ensures a safe environment for your employees and visitors.
The Essential Guide to Alarm Systems: Enhancing Security in the Digital Age

I. Introduction
In our increasingly interconnected world, the significance of robust security measures, such as different types of security alarms, cannot be overstated. Alarm systems, the silent guardians of our digital and physical assets, play a pivotal role in deterring unauthorized access and ensuring the safety of our environments.
The Future of Security Technology: Navigating the New Frontier

Introduction
In our rapidly evolving digital age, the importance of security technology cannot be overstated. The future of IT security is a pivotal concern for industry leaders and individuals alike. As the sophistication of threats continues to escalate, staying abreast of the latest trends in new security technology is not just advisable; it's imperative.
The Essential Guide to Access Control Systems: Enhancing Security in a Modern World

Introduction
Navigating the complexities of modern security can be daunting, but with the right tools, it's entirely manageable. Enter the realm of access control systems, a cornerstone of contemporary security strategies. At BCS Consultants, we understand the critical need to regulate entry and exit within various environments, ensuring that only authorized individuals can access certain areas.


